工单节点使用指南
• 请用平和的语言准确描述你所遇到的问题
• 厂商的技术支持和你一样也是有喜怒哀乐的普通人类,尊重是相互的
• 如果是关于 V2EX 本身的问题反馈,请使用 反馈 节点
这是一个创建于 2147 天前的主题,其中的信息可能已经有所发展或是发生改变。
所有的 github pages 页面开启 HTTPS 的话证书都变成下面这个了?什么情况?
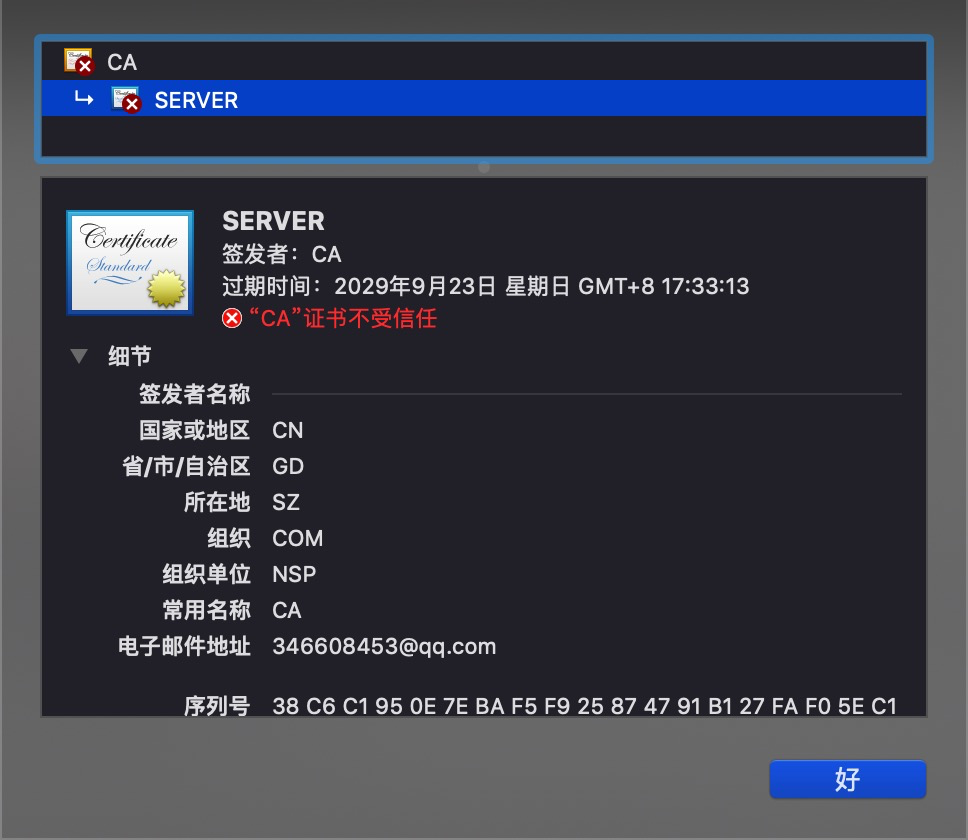
1
twoyuan 2020 年 3 月 26 日
来自 “[email protected]” 的中间人攻击
|
2
WoodenRobot OP @twoyuan 手机网络也是一样的,WiFi 也一样?有点奇怪啊
|
3
xiri 2020 年 3 月 26 日
这个电子邮件地址明显就有问题吧
|
4
SpringHack 2020 年 3 月 26 日
+1,自己的 github pages 也是这个
|
5
alphardex 2020 年 3 月 26 日
同样也碰到了这个问题
|
6
WoodenRobot OP @xiri 对明显的有问题,还能搜到那个人 QQ 号,加好友不通过
|
7
Livid MOD PRO 解析出来的服务器 IP 是?
|
8
bin21st 2020 年 3 月 26 日
@WoodenRobot 我也是这样,然后谷歌搜到了这个页面
|
9
WoodenRobot OP @Livid 185.199.111.153 我自己的是这个,这就是 GitHub 的服务器地址
|
10
WoodenRobot OP 里面 QQ 搜到是这个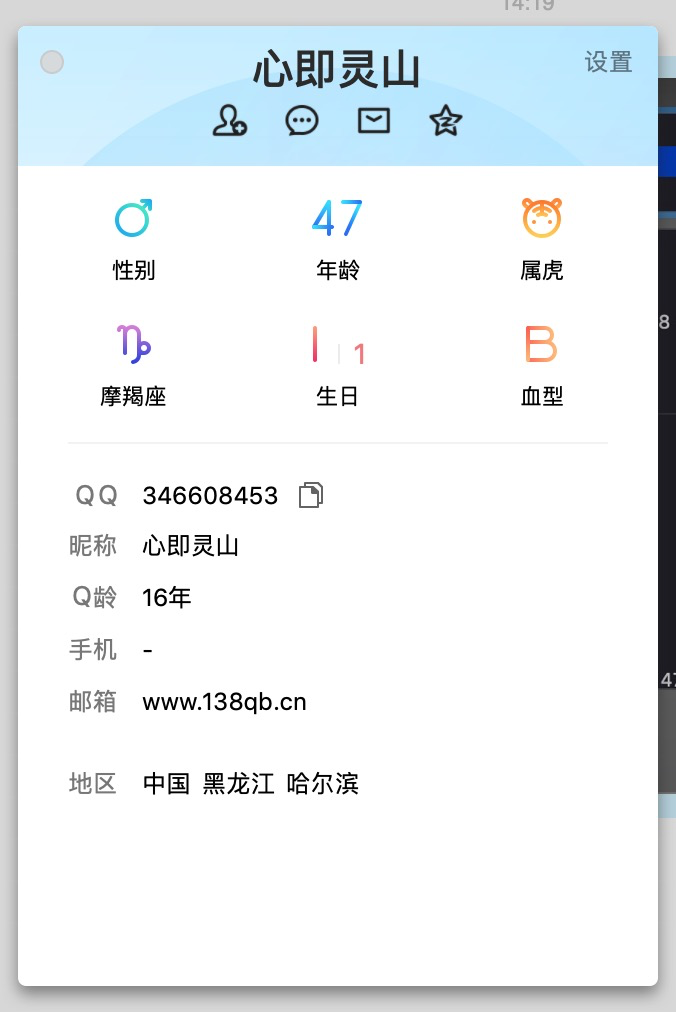
|
11
Livid MOD PRO 贴一下 curl -k -v 访问你的 GitHub Pages 的记录?
|
12
Melodyer 2020 年 3 月 26 日
同!!
|
13
Melodyer 2020 年 3 月 26 日
@Livid
➜ ~ curl -k -v githubstatus.com * Trying 185.199.109.153... * TCP_NODELAY set * Connected to githubstatus.com (185.199.109.153) port 80 (#0) > GET / HTTP/1.1 > Host: githubstatus.com > User-Agent: curl/7.64.1 > Accept: */* > < HTTP/1.1 301 Moved Permanently < Content-Type: text/html < Server: GitHub.com < Location: https://githubstatus.com/ < X-GitHub-Request-Id: F20A:6F7C:2B28AA:2D7250:5E7C4D04 < Content-Length: 162 < Accept-Ranges: bytes < Date: Thu, 26 Mar 2020 06:34:44 GMT < Via: 1.1 varnish < Age: 0 < Connection: keep-alive < X-Served-By: cache-hnd18728-HND < X-Cache: MISS < X-Cache-Hits: 0 < X-Timer: S1585204484.464009,VS0,VE170 < Vary: Accept-Encoding < X-Fastly-Request-ID: 1a3048f21b2a3e7f00c0e09aeae99a8a47d088ed < <html> <head><title>301 Moved Permanently</title></head> <body> <center><h1>301 Moved Permanently</h1></center> <hr><center>nginx</center> </body> </html> * Connection #0 to host githubstatus.com left intact * Closing connection 0 ➜ ~ |
14
Xusually 2020 年 3 月 26 日
@WoodenRobot 根据 qq 信息的域名
Domain Name: 138qb.cn ROID: 20091121s10001s80146151-cn Domain Status: clientTransferProhibited Registrant ID: 120411033010813 Registrant: 广州名扬信息科技有限公司 Registrant Contact Email: **[email protected] Sponsoring Registrar: 广州名扬信息科技有限公司 Name Server: ns1.dnparking.com Name Server: ns2.dnparking.com Name Server: ns3.dnparking.com Name Server: ns4.dnparking.com Registration Time: 2009-11-21 04:27:12 Expiration Time: 2020-11-21 04:27:12 DNSSEC: unsigned |
15
showmethetalk 2020 年 3 月 26 日
+1 我也这样了。。
|
16
leadream4 2020 年 3 月 26 日
我的也是,全局可以访问,好奇怪。
|
17
fuergaosi 2020 年 3 月 26 日
访问 jestjs.io 遇到了同样的问题
 Server: 114.114.114.114 Address: 114.114.114.114#53 Non-authoritative answer: Name: jestjs.io Address: 185.199.108.153 Name: jestjs.io Address: 185.199.111.153 Name: jestjs.io Address: 185.199.110.153 Name: jestjs.io Address: 185.199.109.153 看起来是跟上面一样解析到了一个 ip 上,是 dns 劫持,还是 dns 有问题呢? 另外手机访问也同样遇到了这个证书。 |
18
WoodenRobot OP @Livid
``` $ curl -k -v https://woodenrobot.me * Rebuilt URL to: https://woodenrobot.me/ * Trying 185.199.108.153... * TCP_NODELAY set * Connected to woodenrobot.me (185.199.108.153) port 443 (#0) * ALPN, offering h2 * ALPN, offering http/1.1 * Cipher selection: ALL:!EXPORT:!EXPORT40:!EXPORT56:!aNULL:!LOW:!RC4:@STRENGTH * successfully set certificate verify locations: * CAfile: /etc/ssl/cert.pem CApath: none * TLSv1.2 (OUT), TLS handshake, Client hello (1): * TLSv1.2 (IN), TLS handshake, Server hello (2): * TLSv1.2 (IN), TLS handshake, Certificate (11): * TLSv1.2 (IN), TLS handshake, Server key exchange (12): * TLSv1.2 (IN), TLS handshake, Server finished (14): * TLSv1.2 (OUT), TLS handshake, Client key exchange (16): * TLSv1.2 (OUT), TLS change cipher, Client hello (1): * TLSv1.2 (OUT), TLS handshake, Finished (20): * TLSv1.2 (IN), TLS change cipher, Client hello (1): * TLSv1.2 (IN), TLS handshake, Finished (20): * SSL connection using TLSv1.2 / ECDHE-ECDSA-AES128-GCM-SHA256 * ALPN, server did not agree to a protocol * Server certificate: * subject: C=CN; ST=GD; L=SZ; O=COM; OU=NSP; CN=SERVER; [email protected] * start date: Sep 26 09:33:13 2019 GMT * expire date: Sep 23 09:33:13 2029 GMT * issuer: C=CN; ST=GD; L=SZ; O=COM; OU=NSP; CN=CA; [email protected] * SSL certificate verify result: self signed certificate in certificate chain (19), continuing anyway. > GET / HTTP/1.1 > Host: woodenrobot.me > User-Agent: curl/7.54.0 > Accept: */* ``` |
19
WoodenRobot OP @fuergaosi 这些地址都是 GitHub pages 的服务器,他应该用的 GitHub pages
|
20
Windelight 2020 年 3 月 26 日 via Android
遇到了同样的问题,河北联通。
|
21
U7Q5tLAex2FI0o0g 2020 年 3 月 26 日
亲测,不番羽确实那样,番羽了只后不会
|
22
Livid MOD PRO @WoodenRobot 那么 curl 加了 -k 之后能加载出来你网站上本来的内容么?
|
23
WoodenRobot OP @Livid sorry, 代码块有问题
不能每个回复都有外链, 我把下面我的域名用 xxxx 代替了 $ curl -k -v xxxx * Rebuilt URL to: xxxx * Trying 185.199.108.153... * TCP_NODELAY set * Connected to xxxx (185.199.108.153) port 443 (#0) * ALPN, offering h2 * ALPN, offering http/1.1 * Cipher selection: ALL:!EXPORT:!EXPORT40:!EXPORT56:!aNULL:!LOW:!RC4:@STRENGTH * successfully set certificate verify locations: * CAfile: /etc/ssl/cert.pem CApath: none * TLSv1.2 (OUT), TLS handshake, Client hello (1): * TLSv1.2 (IN), TLS handshake, Server hello (2): * TLSv1.2 (IN), TLS handshake, Certificate (11): * TLSv1.2 (IN), TLS handshake, Server key exchange (12): * TLSv1.2 (IN), TLS handshake, Server finished (14): * TLSv1.2 (OUT), TLS handshake, Client key exchange (16): * TLSv1.2 (OUT), TLS change cipher, Client hello (1): * TLSv1.2 (OUT), TLS handshake, Finished (20): * TLSv1.2 (IN), TLS change cipher, Client hello (1): * TLSv1.2 (IN), TLS handshake, Finished (20): * SSL connection using TLSv1.2 / ECDHE-ECDSA-AES128-GCM-SHA256 * ALPN, server did not agree to a protocol * Server certificate: * subject: C=CN; ST=GD; L=SZ; O=COM; OU=NSP; CN=SERVER; [email protected] * start date: Sep 26 09:33:13 2019 GMT * expire date: Sep 23 09:33:13 2029 GMT * issuer: C=CN; ST=GD; L=SZ; O=COM; OU=NSP; CN=CA; [email protected] * SSL certificate verify result: self signed certificate in certificate chain (19), continuing anyway. > GET / HTTP/1.1 > Host: xxxx > User-Agent: curl/7.54.0 > Accept: */* |
24
xg4 2020 年 3 月 26 日
+1 刚刚访问提示网站风险,还以为输错了地址,看了下证书,发现有个 qq 号的邮箱,google qq 号找到这个
|
25
showmethetalk 2020 年 3 月 26 日
@Livid #22 可以加载
|
26
Windelight 2020 年 3 月 26 日 pi@raspberrypi:~ $ curl -k -v https://zongsoft.github.io
* Expire in 0 ms for 6 (transfer 0x1a44770) -------- Something Similar -------- * Expire in 200 ms for 1 (transfer 0x1a44770) * Trying 185.199.111.153... * TCP_NODELAY set * Expire in 148365 ms for 3 (transfer 0x1a44770) * Expire in 200 ms for 4 (transfer 0x1a44770) * Connected to zongsoft.github.io (185.199.111.153) port 443 (#0) * ALPN, offering h2 * ALPN, offering http/1.1 * successfully set certificate verify locations: * CAfile: none CApath: /etc/ssl/certs * TLSv1.3 (OUT), TLS handshake, Client hello (1): * TLSv1.3 (IN), TLS handshake, Server hello (2): * TLSv1.2 (IN), TLS handshake, Certificate (11): * TLSv1.2 (IN), TLS handshake, Server key exchange (12): * TLSv1.2 (IN), TLS handshake, Server finished (14): * TLSv1.2 (OUT), TLS handshake, Client key exchange (16): * TLSv1.2 (OUT), TLS change cipher, Change cipher spec (1): * TLSv1.2 (OUT), TLS handshake, Finished (20): * TLSv1.2 (IN), TLS handshake, Finished (20): * SSL connection using TLSv1.2 / ECDHE-ECDSA-AES128-GCM-SHA256 * ALPN, server did not agree to a protocol * Server certificate: * subject: C=CN; ST=GD; L=SZ; O=COM; OU=NSP; CN=SERVER; [email protected] * start date: Sep 26 09:33:13 2019 GMT * expire date: Sep 23 09:33:13 2029 GMT * issuer: C=CN; ST=GD; L=SZ; O=COM; OU=NSP; CN=CA; [email protected] * SSL certificate verify result: self signed certificate in certificate chain (19), continuing anyway. > GET / HTTP/1.1 > Host: zongsoft.github.io > User-Agent: curl/7.64.0 > Accept: */* > 奇怪的是不能加载出任何内容 |
27
lovedebug 2020 年 3 月 26 日
江苏电信测试结果也是重定向到 185.199.111.153
|
28
WoodenRobot OP @Livid 国内访问加载不全,只能加载一部分就出现下面内容中断了,国外访问没问题
* LibreSSL SSL_read: SSL_ERROR_SYSCALL, errno 54 * stopped the pause stream! * Closing connection 0 curl: (56) LibreSSL SSL_read: SSL_ERROR_SYSCALL, errno 54 |
29
WoodenRobot OP |
30
AoTmmy 2020 年 3 月 26 日 via Android
联通复现
|
31
caola 2020 年 3 月 26 日
我的好几个域名都这样,造成无法访问,持续了大半天时间
|
32
YS5RhZIi09QH7T9D 2020 年 3 月 26 日
|
33
mcone 2020 年 3 月 26 日
怎么感觉是中间人公鸡
|
34
LaTero 2020 年 3 月 26 日
dns 没问题的,海外 curl --resolve xxx:443:185.199.108.153 xxxps://xxx 可以正常访问。
|
35
jiejiss 2020 年 3 月 26 日
移动没有复现
TL;DR issuer: C=US; O=Let's Encrypt; CN=Let's Encrypt Authority X3; issuer: C=US; O=DigiCert Inc; OU=www.digicert.com; CN=DigiCert SHA2 High Assurance Server CA * Rebuilt URL to: https://woodenrobot.me/ * Trying 185.199.108.153... * TCP_NODELAY set * Connected to woodenrobot.me (127.0.0.1) port 443 (#0) * ALPN, offering h2 * ALPN, offering http/1.1 * Cipher selection: ALL:!EXPORT:!EXPORT40:!EXPORT56:!aNULL:!LOW:!RC4:@STRENGTH * successfully set certificate verify locations: * CAfile: /etc/ssl/cert.pem CApath: none * // ... ... * SSL connection using TLSv1.2 / ECDHE-RSA-AES128-GCM-SHA256 * ALPN, server accepted to use h2 * Server certificate: * subject: CN=woodenrobot.me * start date: Feb 2 09:35:52 2020 GMT * expire date: May 2 09:35:52 2020 GMT * issuer: C=US; O=Let's Encrypt; CN=Let's Encrypt Authority X3 * SSL certificate verify ok. * Using HTTP2, server supports multi-use * Connection state changed (HTTP/2 confirmed) * Copying HTTP/2 data in stream buffer to connection buffer after upgrade: len=0 * Using Stream ID: 1 (easy handle 0x7fa13b004400) > GET / HTTP/2 > Host: woodenrobot.me > User-Agent: curl/7.54.0 > Accept: */* > * Connection state changed (MAX_CONCURRENT_STREAMS updated)! ^C * Rebuilt URL to: https://zongsoft.github.io/ * Trying 185.199.111.153... * TCP_NODELAY set * Connected to zongsoft.github.io (127.0.0.1) port 443 (#0) * ALPN, offering h2 * ALPN, offering http/1.1 * Cipher selection: ALL:!EXPORT:!EXPORT40:!EXPORT56:!aNULL:!LOW:!RC4:@STRENGTH * successfully set certificate verify locations: * CAfile: /etc/ssl/cert.pem CApath: none * // ... ... * SSL connection using TLSv1.2 / ECDHE-RSA-AES128-GCM-SHA256 * ALPN, server accepted to use h2 * Server certificate: * subject: C=US; ST=California; L=San Francisco; O=GitHub, Inc.; CN=www.github.com * start date: Jun 27 00:00:00 2018 GMT * expire date: Jun 20 12:00:00 2020 GMT * issuer: C=US; O=DigiCert Inc; OU=www.digicert.com; CN=DigiCert SHA2 High Assurance Server CA * SSL certificate verify ok. * Using HTTP2, server supports multi-use * Connection state changed (HTTP/2 confirmed) * Copying HTTP/2 data in stream buffer to connection buffer after upgrade: len=0 * Using Stream ID: 1 (easy handle 0x7feb0b000000) > GET / HTTP/2 > Host: zongsoft.github.io > User-Agent: curl/7.54.0 > Accept: */* > * Connection state changed (MAX_CONCURRENT_STREAMS updated)! ^C |
36
Windelight 2020 年 3 月 26 日 via Android
这个 ip 地址的确是连接到了 Github 的服务器,美国 GitHub#Fastly,纯真查的,然后这个证书信息有个大概的地址写的是 CN GD SZ COM NSP,QQ 号 346608453,一个哈尔滨大哥
|
37
J0G57faC6uPo75W0 2020 年 3 月 26 日
没有代理时 遇到了同样的问题.
错误是:" FetchEvent.respondWith received an error TypeError: 此服务器的证书无效. 您可能正在连接到一个伪装成"网址"的服务器. 嗯, 提示很明显了. 上了代理就正常了. hah, 这件事终于要发生了嘛... |
38
xiri 2020 年 3 月 26 日
上面你们发的那几个地址加上代理就没有问题,国内直接访问确实证书都存在问题,有人在大范围劫持?中间人攻击?
|
39
gz911122 2020 年 3 月 26 日
我的也是这样 ,从 google 搜到了这个帖子
|
40
SomeBottle 2020 年 3 月 26 日
博客上了亚太 cdn 倒是没问题,大陆访问直接就证书错误了...那个 QQ 号看上去也像是顶锅的
|
41
lishu5566 2020 年 3 月 26 日
全局代理证书就正常了;有什么大的事情要发生吗 ?
|
42
SaigyoujiYuyuko 2020 年 3 月 26 日
看起来是中间人?... 使用 55r 代理证书正常 直接连接证书错误
|
43
chinvo 2020 年 3 月 26 日
解析出来的 IP 是对的, 但是访问过去证书错误
这么大规模的 IP 劫持, 细思恐极 |
44
Greatshu 2020 年 3 月 26 日
吓死我了,还以为我的博客被认证了。结果是大规模劫持啊,放心了。
|
45
genezx 2020 年 3 月 26 日
上海、浙江、湖北、广东、电信、联通全部中招,看来国内都中招了
|
46
zackwu 2020 年 3 月 26 日
浙江移动,未能复现。
|
47
HXM 2020 年 3 月 26 日 via Android
可复现
|
48
zst 2020 年 3 月 26 日 via Android
电信 4G 复现了
|
49
Windelight 2020 年 3 月 26 日
这大哥也太不认真了,叫啥住哪长啥样都靠一个 qq 出来了。
但是我认为他可能只是一个运维或者码农,签了一个内部测试用的证书 然后不知道被谁拿去配置错了-_-|| 结果还是可能某个中间的 CDN 或者审查服务器上。 希望这大哥能保住工作吧,就算给他祈福了。 希望 Fastly 可以不太 Fastly |
50
xiri 2020 年 3 月 26 日
刚刚发现不只是这些博客,https://pages.github.com/ 也证书错误了
|
51
caishuhao2000 2020 年 3 月 26 日
上海电信复现
|
52
billchenchina 2020 年 3 月 26 日 via Android
|
53
rayhy 2020 年 3 月 26 日
山西联通复现
|
54
isukkaw 2020 年 3 月 26 日 Fastly 其他服务都没影响,唯独 GitHub 交给 Fastly 代播的 IP 炸了,多半是国内哪个 xx 不小心路由风暴了
|
55
mom0a 2020 年 3 月 26 日
辽宁联通复现
|
56
est 2020 年 3 月 26 日
向当地通管局举报。破坏信息系统。
|
57
billchenchina 2020 年 3 月 26 日
#54 @isukkawicmp mtr 没炸,
|
58
lishu5566 2020 年 3 月 26 日
有没有大神,人肉一下这个 QQ !估计是个背锅侠。
|
59
billchenchina 2020 年 3 月 26 日
#54 @isukkaw
icmp mtr 没炸,仍然是 ntt - fastly 。单纯 TCP 劫持了 |
60
chenshaoju 2020 年 3 月 26 日 |
61
jhdsgfww 2020 年 3 月 26 日
补充一下,山东移动也不行(至少我所在的地区不行)
|
62
isukkaw 2020 年 3 月 26 日
@billchenchina #59 看了一下,仅 443 TCP 会在广州电信这一跳被劫持掉。
|
63
U7Q5tLAex2FI0o0g 2020 年 3 月 26 日
最新:github.com 也中了
|
64
xolor 2020 年 3 月 26 日
希望是暂时的,不要变为常态呀...
|
65
rayhy 2020 年 3 月 26 日
@littleylv 我这里 github.com 暂时没炸,只有 github pages
|
66
YS5RhZIi09QH7T9D 2020 年 3 月 26 日
@xolor 我昨天下午就遇到了。。。
|
67
U7Q5tLAex2FI0o0g 2020 年 3 月 26 日
|
68
FIyingSky 2020 年 3 月 26 日
浙江移动,未能复现……
|
69
unifier 2020 年 3 月 26 日
山东联通中招
|
70
Howard2000 2020 年 3 月 26 日 广东移动复现
|
71
fanyuxi 2020 年 3 月 26 日
刚刚发现同样的问题,在 bing 搜了一下这个邮箱,搜到这个帖子。
(广州电信) |
72
mzlogin 2020 年 3 月 26 日
+1,武汉电信复现
``` ~$ curl -k -v https://mazhuang.org [master] * Trying 185.199.108.153... * TCP_NODELAY set * Connected to mazhuang.org (185.199.108.153) port 443 (#0) * ALPN, offering h2 * ALPN, offering http/1.1 * successfully set certificate verify locations: * CAfile: /etc/ssl/cert.pem CApath: none * TLSv1.2 (OUT), TLS handshake, Client hello (1): * TLSv1.2 (IN), TLS handshake, Server hello (2): * TLSv1.2 (IN), TLS handshake, Certificate (11): * TLSv1.2 (IN), TLS handshake, Server key exchange (12): * TLSv1.2 (IN), TLS handshake, Server finished (14): * TLSv1.2 (OUT), TLS handshake, Client key exchange (16): * TLSv1.2 (OUT), TLS change cipher, Change cipher spec (1): * TLSv1.2 (OUT), TLS handshake, Finished (20): * TLSv1.2 (IN), TLS change cipher, Change cipher spec (1): * TLSv1.2 (IN), TLS handshake, Finished (20): * SSL connection using TLSv1.2 / ECDHE-ECDSA-AES128-GCM-SHA256 * ALPN, server did not agree to a protocol * Server certificate: * subject: C=CN; ST=GD; L=SZ; O=COM; OU=NSP; CN=SERVER; [email protected] * start date: Sep 26 09:33:13 2019 GMT * expire date: Sep 23 09:33:13 2029 GMT * issuer: C=CN; ST=GD; L=SZ; O=COM; OU=NSP; CN=CA; [email protected] * SSL certificate verify result: self signed certificate in certificate chain (19), continuing anyway. ``` |
73
zackwu 2020 年 3 月 26 日
完了,用 https://17ce.com/ 测试下来,全国大部分地区都中招了。
|
74
fenghuang 2020 年 3 月 26 日
这个劫持是怎么实现的呢
|
75
Valid 2020 年 3 月 26 日
在座的各位肯定都查了那个 qq
|
77
Windelight 2020 年 3 月 26 日
@lishu5566 新法规已于 3 月 1 号实行了 :-)
icmp4 跳的是 AS4837 - AS2914 - AS54113 17ce 测试,全国只有中部个别地区正常 http://www.17ce.com/site/http/20200326_7ee6f8306f3411eab8bc2bbb7b33a12c:1.html |
78
hpx9797 2020 年 3 月 26 日
内蒙联通复线 github 相关一些域名经常打不开
|
79
dven 2020 年 3 月 26 日
大概是某个 ISP 或 IDC 漏路由,但具体是谁,不好确定
|
81
002jnm 2020 年 3 月 26 日
C:\Users\admin>tcping 185.199.109.153 443
Probing 185.199.109.153:443/tcp - Port is open - time=6.733ms Probing 185.199.109.153:443/tcp - Port is open - time=6.790ms Probing 185.199.109.153:443/tcp - Port is open - time=5.762ms Probing 185.199.109.153:443/tcp - Port is open - time=5.417ms |
82
EdPlaysMC 2020 年 3 月 26 日
广东电信复现,似乎是劫持了 443 端口,80 端口正常日本 NTT
|
83
hszhakka2ex 2020 年 3 月 26 日
|
84
Ansonyi 2020 年 3 月 26 日
浙江金华移动电信复现
|
86
chenshaoju 2020 年 3 月 26 日 |
87
xnotepad 2020 年 3 月 26 日
浙江联通流量好像可以访问了,速度还挺快的,不知道是不是暂时的。
|
88
Sk3y 2020 年 3 月 26 日
大连电信已复现该错误。
这个 QQ 是哪位高人的... |
89
lishu5566 2020 年 3 月 26 日
@Windelight Got it !
|
90
Kangnakamuyi 2020 年 3 月 26 日
河北联通 4G 也炸了
这 Fastly 今天是怎么回事啊...... |
91
Esen 2020 年 3 月 26 日
暂时关闭了 https,虽然没人访问我的 pages
|
92
jiejiss 2020 年 3 月 26 日
北京移动,https://desktop.github.com/ 中招,估计别的网址也一样
|
93
skyeycirno 2020 年 3 月 26 日
黑龙江电信没问题。一切正常。。
|
94
codingAlex 2020 年 3 月 26 日
安徽电信,一切正常啊。
|
95
INTEL2333 2020 年 3 月 26 日
广州电信挂了,应该是劫持到本地的了,平均 tcping443 的延迟 3ms
|
97
yEhwG10ZJa83067x 2020 年 3 月 26 日
浙江电信,复现
|
98
yulihao 2020 年 3 月 26 日
阿里云上海复现
Tracing route to github.io:443 1 2044 ms timed out 1 2001 ms timed out 1 2002 ms timed out 2 21 ms 11.53.4.217 TimeExceeded 3 2002 ms timed out 3 2001 ms timed out 3 2001 ms timed out 4 2 ms 10.255.106.101 TimeExceeded 5 24 ms 103.49.76.110 TimeExceeded 6 3 ms 116.251.113.189 TimeExceeded 7 2003 ms timed out 7 2001 ms timed out 7 2002 ms timed out 8 7 ms 101.95.208.33 TimeExceeded 9 13 ms 124.74.166.9 TimeExceeded 10 16 ms 101.95.120.198 TimeExceeded 11 11 ms 185.199.109.153:443 Synchronize, Acknowledgment (port open) |
99
rssvtwoex 2020 年 3 月 26 日
深圳电信复现
|
100
alect 2020 年 3 月 26 日
套一层 CloudFlare 可以解决吧?
|